Keycloak is a JWT token provider. In this tutorial, we will use keycloak to provide OIDC tokens to Vault.
Keycloak is a centralized identity management system that can be used to manage user authentication and authorization requests. Keycloak uses OIDC for managing user authentication and authorization requests from external applications.
In this tutorial, we will use Keycloak as an OIDC provider for Vault.
NOTE:
- You need a running and unsealed vault already. The Vault can be accessed at the URL: https://vault.example.com
- You need to have an already running KeyCloak Server to use as the Identity Provider. You also need to configure your Keycloak server with a suitable database. Once this is done and the Vault is unsealed, you can begin configuring Hashicorp Vault for use with Keycloak.
Keycloak
Go to your realmSettings > General> Name = vault.example.com

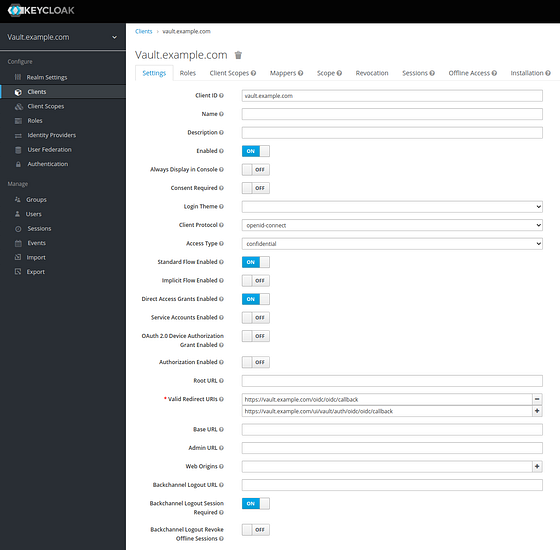
Go to Clients > Add Client. The client ID is vault.example.com and the protocol is openid-connect

- Set the Client Settings to the following
- Client ID = vault.example.com
- Access Type = confidential
- Valid Redirect URIs =
https://vault.example.com/oidc/oidc/callback
https://vault.example.com/ui/vault/auth/oidc/oidc/callback
save
OIDC->Client->Secret (I'll be using this later)

Vault (cli)
export VAULT_TOKEN=<your root or access token>Enable OIDC authentication
$ vault auth enable oidcConfigure the OIDC Provider in cli.
$ vault write auth/oidc/config \
oidc_discovery_url="https://idms.example.com/auth/realms/vault.example.com" \
oidc_client_id="vault.example.com" \
oidc_client_secret="<OIDC-Client-Secret>" \
default_role=readerCreate a policy file reader by creating the file reader.hcl
path "/secret/*" {
capabilities = ["read", "list"]
}Prepare to deploy the policy by importing it into vault.
$ cat reader.hcl | vault policy write reader -Use the deployed role for OIDC configuration
$ vault write auth/oidc/role/reader \
bound_audiences="vault.example.com" \
allowed_redirect_uris="https://vault.example.com/oidc/oidc/callback" \
allowed_redirect_uris="https://vault.example.com/ui/vault/auth/oidc/oidc/callback" \
user_claim="sub" \
policies=readerUse OIDC authentication to log in to Vault with Keycloak.
Go to Vault https://vault.example.com

A new window will appear on your screen, in which you should type the correct user name and password. Once inputting those credentials correctly, please wait a second before closing that popup window.

You can now use Vault according to the policy you created earlier.
Troubleshooting
A custom CA has been implemented for web-certificates.
Error writing data to auth/oidc/config: Error making API request.URL: PUT http://127.0.0.1:8200/v1/auth/oidc/config
Code: 400. Errors:* error checking oidc discovery URL: error creating provider with given values: NewProvider: unable to create provider: Get "https://idms.example.com/auth/realms/vault.example.com/.well-known/openid-configuration": x509: certificate signed by unknown authorityAdd your certificate chain to the request, see step Write the OIDC Configuration

